Complete guide to Cyber Anonymity
No doubt, in this era we have a very strong role-player, who has influenced our life in many ways, that is Internet. Somehow we're getting dependent on internet and not even concerned about our safety and privacy. I want you to see this website stayinvisible. Shocked! To see how much information do they have about you. Even Google record and store much of your information. And we don't know how many websites out there are having personal information of yours, that you won't like. So this guide is for you to stay anonymous and live free without being concerned about your security over the Internet. Consider following options
Proxies
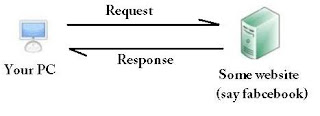
When you don't use proxy:Proxy server is an intermediate server that sends request on
behalf of client, gets response from server and forward it to the client. In usual case when you are not using any proxy
then your connection to any website is like this
Here there is no anonymity for you, the website you access can know
every information of you (including your IP), and hence this connection is transparent.
When you use proxy: now when you access some website through a proxy,
you will send request to the proxy server that will forward that request to the
desired website you want to connect to. Then response given by the website is
gathered by proxy server and further sent to you thereby the website doesn't come to know about the real person asking for request.
How can I use proxy to stay Anonymous?
You
can configure your browser to use some proxy server. To do so first of all go
to hidemyass.com and note down a highly anonymous IP. Now you need to configure your browser to
use this IP. Follow these navigations according to the browser you are using
For Mozilla:
Click on ‘Tools’, then ‘options’. Under the ‘Advance’ tab select ‘Network’ click
‘Settings’ select ‘Manual proxy configuration’ and Enter the IP noted from the
proxy list.
For
Chrome: Click on ‘Customize and control’ button then click on ‘options’, select
‘Under the hood’ and click on ‘Change Proxy Settings’ the Internet option
dialog box will appear, click on ‘LAN Settings’ tick ‘Use proxy server for LAN’
and enter the IP that you noted from IP-list as mentioned above.
There
are some proxy websites too, to use them you don’t need to configure you
browser you can just use their service through their website. Few of them are-
1. Hidemyass
3. Proxite
VPN (Virtual Private Network)
A virtual
private network (VPN) is a secure network that uses
primarily public telecommunication infrastructures, such as the Internet, to
provide remote offices or traveling users an access to a central organizational
network.
There are many
free and paid VPN services available out there. To use these services, you just
have to create an account in their website and download their client. Few of the
best free VPN’s are
1.
ProXPN: It will allow you to surf internet securely
without any chaos. I’ve used the free service for quite some time and found it
pretty good and gets much better if you purchase the pro version.
Website: https://www.proxpn.com/
2.
OpenVPN: OpenVPN is extremely easy to install and
use VPN. Just download the OpenVPN client and you can get yourself paranoid.
3.
CyberGhost: A free utility to make yourself
anonymous. It has a paid version too. While using CyberGhost free version you can
have a session of maximum 1gb data download or 6 hour browsing.
How Do Hackers stay anonymous?
Hacker/crackers who perform criminal activities and still they manage to flee away, usually implement highly sophisticated combination of techniques. They use the options that are discussed above but in addition they implement some other methods too, to achieve maximum anonymity. Few of those issues are
- Virtual OS: Virtual machine is a guest operating system running on the top of host operating system. virtual OS is used to attain high anonymity as usage of guest OS allows user to easily get rid of log file, and gives flexibility to manipulate the MAC address. The most popular virtual machines are VMware and Virtual Box.
- Spoofing MAC address: Every Network interface card has a unique MAC address assigned to it, which is used by forensic to trace hacker. Hence spoofing of MAC address makes it hard to trace a hacker. Mac address can be spoofed manually or by using some software like this.
- TOR's live CD: Use of live cd is another good option that can be used to add to the anonymity.Tor's live cd named as 'tails' can be downloaded from TOR website. All the connections in tails goes through TORs networks and it leaves no evidence of whatever you've done.